
+ Digital SIgnature = C.I.A.
Confusion: each character of the ciphertext should depend on several parts of the key
Diffusion: if we change a character of the plaintext, then several characters of the ciphertext should change,

+ Encryption = C.I.A.
The Digital Signature Standard allows use of DSA, RSA, or ECC in conjunction with SHA-1 to produce secure digital signatures.
Hashes are one-way math -> Cannot be reversed
Collision: when 2 different documents create the same hash
MD5 produces a 128-bit message digest
SHA-1 produces a 160-bit message digest
SHA-256 produces a 256-bit message digest
cryptographist creates
cryptoanalyst tries to break
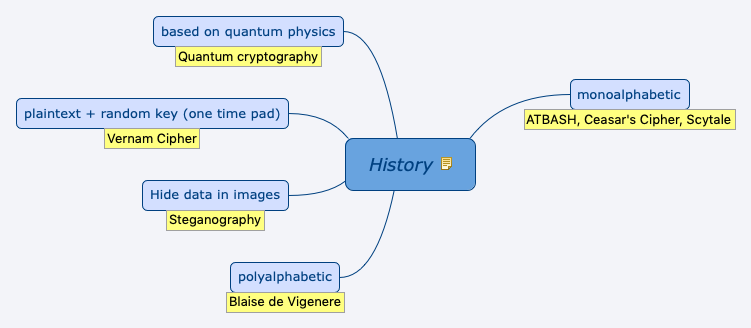
Kerckhoffs, 19th century - "Algo should be public, only key should be secret"
"Security of an algo rests in the key generation" - Bruce Schneier
ATBASH, Ceasar's Cipher, Scytale
Blaise de Vigenere
Steganography
Vernam Cipher
Quantum cryptography
DES, 3DES, AES, IDEA, Twofish, Blowfish, SAFER, Rivest
Shared = Secret
Confidentiality only, No non-repud
+ Fast
- Key distribution, Scalability: n(n-1)/2
Kerberos is a computer-network authentication protocol that builds on Symmetric Key Cryptography
See Also: Encryption, Block Ciphers, Stream Ciphers
Public <> Private
It uses one-way functions which are easy to compute but difficult to reverse.
Key number with n participant = (n * (n-1)) / 2
Advantage:
- It is possible to send a message across an untrusted medium in a secure manner without the overhead of prior key exchange or key material distribution.
Disadvantages:
- Asymmetric cryptography is extremely slow compared to its
symmetric counterpart.
- The ciphertext output may be much larger than the plaintext.
See Also: Encryption, RSA, El Gamal, ECC, DSA, Merkle-Hellman knapsack, Diffie-Hellman
Key size 1,024 to 4,096
Round 1
NIST recommended moving away from 1024-bit RSA key size by the end of 2010
Approaches to attack:
-brute force
- mathematical attacks, factoring the product of two prime
numbers; and timing attacks,
-measuring the running time of the decryption algorithm
See Also: ASYMM
Msg divided into blocks of bits
See Also: SYMM, DES, 3DES, 2DES, AES, IDEA, Blowfish - Twofish, RC5 - RC6, Skipjack
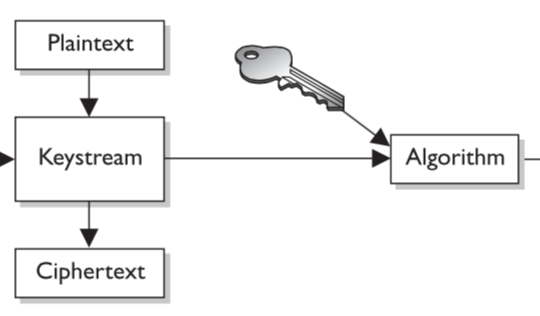
Processes single bit at time.
Plaintext XOR Random cipher bit stream
ALG: Lucifer, BLK: 64, KEY: 56 (+ 8 parity bits), METH: C+D
See Also: Block Ciphers, CBC, OFB, ECB, CFB, CTR
![]()
Electronic Code Book (the simplest and weakest mode)
plaintext + key = always gives same ciphertext
See Also: DES
![]()
Cipher Block Chaining (uses chaining to destroy patterns, but errors can propagate)
Some ciphertext created from the previous block is inserted into the next one.
See Also: DES
![]()
Cipher Feedback Mode
Emulates a stream cipher and can be used to encrypt individual characters. Errors can propagate.
Ciphertext from previous block + Key -> Encrypts plaintext
See Also: DES
Output Feedback Mode
Initialization Vector (IV) used.
Values used to encrypt the next block of plaintext are coming directly from the keystream -> Errors do not propagate -> better way to encrypt error sensitive data (digitized video or voice signal)
It turns a block cipher into a synchronous stream cipher.
See Also: DES
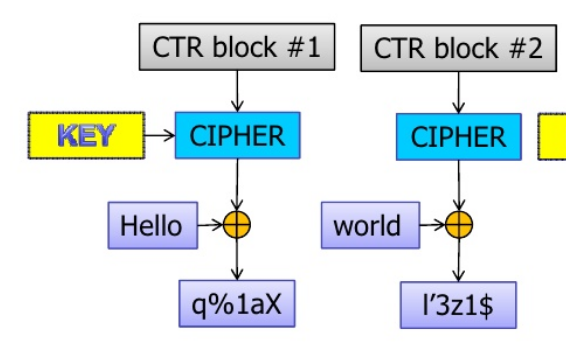
COUNTER (CTR) turns a block cipher into a stream cipher.
It uses a counter as feedback. Errors do not propagate.
See Also: DES
BLK LGTH: 64, KEY LGTH: 168, METH: C+D
Applies Single DES encryption 3 times. Recommended standard since 1999.
See Also: Block Ciphers, DES EEE2, DES EDE2, DES EEE3, DES EDE3
Encrypted 3 times with 2 keys
Key1 Encrypts -> Key2 Encrypts -> Key1 Encrypts
See Also: 3DES
Key1 Encrypts -> Key2 Decrypts -> Key1 Encrypts
See Also: 3DES
Plaintext encrypted 3 times using 3 different keys
See Also: 3DES
Key1 Encrypts -> Key2 Decrypts -> Key3 Encrypts
(2 layers of encryption)
See Also: 3DES
Key length: 112 bit.
It is not more secure than DES. Same work factor to crack as demonstrated by the Meet-in-the-middle attack.
See Also: Block Ciphers
Advanced Encryption Standard aka Rijndael
U.S. Standard - NIST 2002
Block: 128
Key / Rounds:
128 / 10
192 / 12
256 /15
Round:
SubBytes > ShiftRows > MixColumns > AddRoundKey
See Also: Block Ciphers
International Data Encryption Algorithm
Block length: 64
Key length: 128
Designed as International replacement to DES.
It's at the base of PGP.
See Also: Block Ciphers
![]()
Blow
Block: 64
Key: 32 -448 Key
Two
Block:128
Key: 128 - 256
Developed to meet AES requirements.
Uses prewhitening and postwhitening: additional subkeys are XORed into the text block both before the first round and after the last round.
See Also: Block Ciphers
RC5
Block: 32, 64 or 128
Key: 0 - 2040 (128 suggested)
Rounds: 1 - 255 (12 suggested)
RC6
Block: 128
Key: 128, 192, 256
Rounds: 20
See Also: Block Ciphers
It is a method of securely exchanging cryptographic keys over a public channel. It is not for encryption or decryption.
See Also: ASYMM
Asymmetric key encryption algorithm for public-key cryptography which is based on the Diffie–Hellman key exchange.
DSA is based on El Gamal.
A general ElGamal encryption produces a 2:1 expansion in size from plaintext to ciphertext.
See Also: ASYMM
Elliptic Curve Cryptography.
The elliptic curve algorithms have the highest strength per bit of key length of any of the asymmetric algorithms.
See Also: ASYMM
Developed by the US government for digital signatures. It can be used only for signing data and it cannot be used for encryption.
Although intended to have a maximum key size of 1,024 bits, longer key sizes are now supported.
It is based on El Gamal.
See Also: ASYMM
Combines the strengths of both symmetric cryptography (great speed and secure algorithms) and asymmetric cryptography (ability to securely exchange session keys, message authentication, and
nonrepudiation).
Asymmetric cryptography can handle the initial setup of the communications session through the exchange or negotiation of the symmetric keys to be used for this session.
All practical implementations of public key cryptography today employ the use of a hybrid system. Examples include the TLS protocol which uses a public-key mechanism for key exchange (such as Diffie-Hellman) and a symmetric-key mechanism for data encapsulation (such as AES)
See Also: Encryption
Block: 64
Key: 80
See Also: Block Ciphers
Key size: 40 - 2048
Multiple vulnerabilities have been discovered in RC4, rendering it insecure.
Particularly problematic uses of RC4 have led to very insecure protocols such as WEP.
See Also: Stream Ciphers
![]()
It can be implemented faster than RSA, yet it was found insecure.
Unlike RSA, it is one-way: the public key is used only for encryption, and the private key is used only for decryption. Thus it is unusable for authentication by cryptographic signing.
See Also: ASYMM